Knowledge Management: Difference between revisions
No edit summary |
No edit summary |
||
| Line 3: | Line 3: | ||
</br> | </br> | ||
In Secure Group, we developed a culture in which people can feel independent and autonomous when working. We believe traditional rigid management structures do not create a supportive environment, but cause unnecessary stress and distracts employees, which jeopardizes performance. Because of that, we respect our people's skills and knowledge and support them to pursue the company’s goals in their own way. This mutual respect between parties is essential to our Knowledge Management strategy | In Secure Group, we developed a culture in which people can feel independent and autonomous when working. We believe traditional rigid management structures do not create a supportive environment, but cause unnecessary stress and distracts employees, which jeopardizes performance. Because of that, we respect our people's skills and knowledge and support them to pursue the company’s goals in their own way. This mutual respect between parties is essential to our Knowledge Management strategy and we can only afford this level of trust in our people if we know they are fully capable of doing their work and can fill any knowledge gaps quickly and efficiently. | ||
It's a no-brainer that knowledge enables us to grow and innovate. But, it's a fact also that this is easier said than done. Before we reached our ideal Knowledge Management strategy, we faced some problems. The old way we managed information at Secure Group was inefficient. Information was shared in a fragmented way, through email and messaging apps. When people needed information, they’d go to an expert and ask them, which not only wasted time but would only benefit one person. It was difficult for the person to retain the new information, especially if it was shared in passing conversation or buried among emails. The process was also not being overseen, so embellishments and inaccuracies could slip through, which could jeopardize the information. Finally, when a knowledge gap formed, we had no way to fill it, as the one-to-one nature of knowledge sharing was impossible to scale, and the gap would remain. | |||
</br> | </br> | ||
After learning from these past mistakes, we then decided where knowledge should '''NOT''' be. We realized our knowledge should be easily accessible by our team. It should not be stuck in someone’s head, where it is of no use to anyone but the person - it would even be unhelpful since people would constantly interrupt their work with questions. It should also not be chaotically thrown around emails and messages, where it is impossible to track and collect. Nor should it be dumped in guides and manuals and be forgotten about, becoming obsolete and misleading. | |||
We also knew that each of the generations has a different way of learning, advancing and collaborating. We recognized this by sharing knowledge in two formats. These are reading and face to face courses with a practical application. | We also knew that each of the generations has a different way of learning, advancing and collaborating. We recognized this by sharing knowledge in two formats. These are reading and face to face courses with a practical application. | ||
Revision as of 11:26, 21 April 2021
The Secure Group knowledge management strategy enables our organization to create, apply, and share information, breaking down silos and increasing the usage of valuable data.
In Secure Group, we developed a culture in which people can feel independent and autonomous when working. We believe traditional rigid management structures do not create a supportive environment, but cause unnecessary stress and distracts employees, which jeopardizes performance. Because of that, we respect our people's skills and knowledge and support them to pursue the company’s goals in their own way. This mutual respect between parties is essential to our Knowledge Management strategy and we can only afford this level of trust in our people if we know they are fully capable of doing their work and can fill any knowledge gaps quickly and efficiently.
It's a no-brainer that knowledge enables us to grow and innovate. But, it's a fact also that this is easier said than done. Before we reached our ideal Knowledge Management strategy, we faced some problems. The old way we managed information at Secure Group was inefficient. Information was shared in a fragmented way, through email and messaging apps. When people needed information, they’d go to an expert and ask them, which not only wasted time but would only benefit one person. It was difficult for the person to retain the new information, especially if it was shared in passing conversation or buried among emails. The process was also not being overseen, so embellishments and inaccuracies could slip through, which could jeopardize the information. Finally, when a knowledge gap formed, we had no way to fill it, as the one-to-one nature of knowledge sharing was impossible to scale, and the gap would remain.
After learning from these past mistakes, we then decided where knowledge should NOT be. We realized our knowledge should be easily accessible by our team. It should not be stuck in someone’s head, where it is of no use to anyone but the person - it would even be unhelpful since people would constantly interrupt their work with questions. It should also not be chaotically thrown around emails and messages, where it is impossible to track and collect. Nor should it be dumped in guides and manuals and be forgotten about, becoming obsolete and misleading.
We also knew that each of the generations has a different way of learning, advancing and collaborating. We recognized this by sharing knowledge in two formats. These are reading and face to face courses with a practical application.
Knowledge sharing is also built into the Levels in our Frameworks. To progress, individuals must demonstrate the capability of sharing knowledge in a structured way and the capability of applying Tech Sessions.
We share knowledge through our internal wiki Confluence. Our wiki acts as a single source of all knowledge for our organization which can be created, edited and modified by any employee. Confluence functions as a central repository for managing and distributing all company knowledge and information. Here, all co-workers can store internal documentation about company policies, processes, how-to guides, projects or products they are building, common workflows, procedure checklists, and more.
Knowledge Categories
In our Management Model and structure of the Career Framework, we are currently assessing knowledge regarding the following categories:
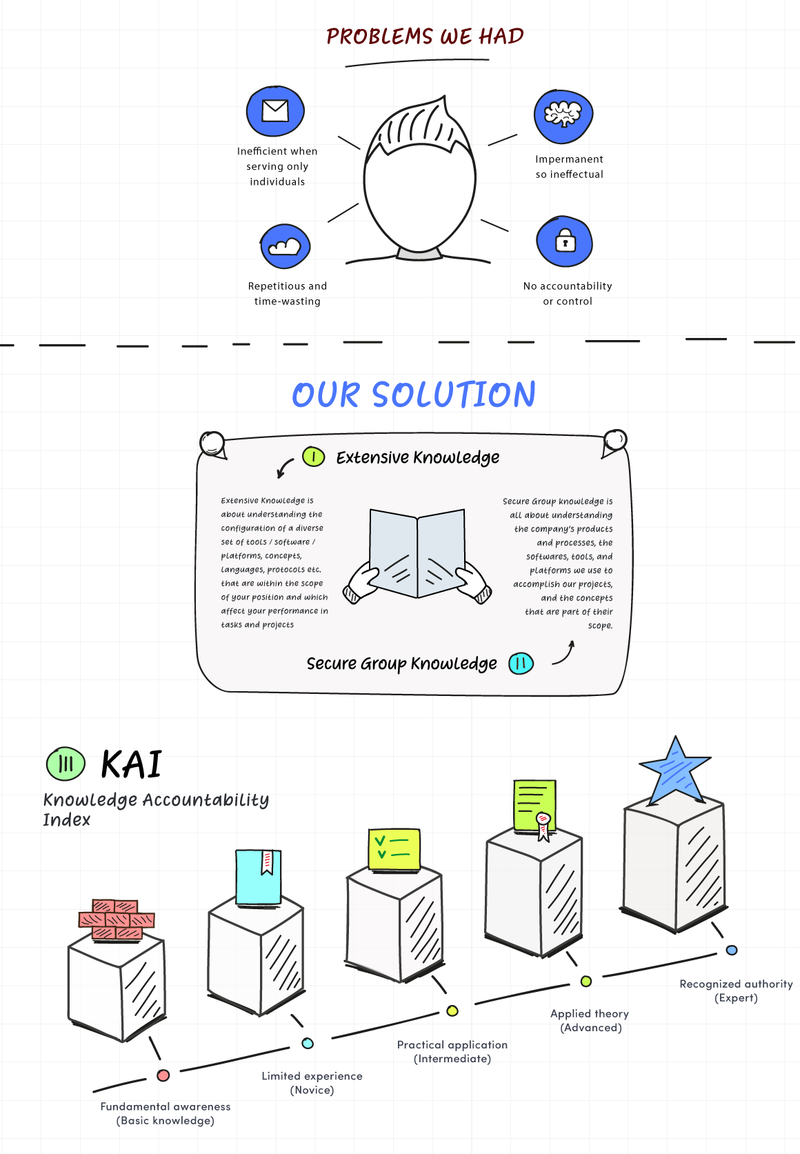
- Extensive Knowledge – this is about understanding the usage and configuration of a diverse set of tools/software/platforms, concepts, languages, protocols etc. which affect your performance within the company. They can be related to the scope of your position but also they can be related to specific knowledge you need to acquire in order to complete tasks and projects in Secure Group. Employees should grow this knowledge and hard skills on their own, while the company will provide context on the application of the tool/software/platform within defined processes.
- Secure Group Knowledge – this is all about understanding the company’s products and processes, the way all teams work, the concepts that are part of their scope and how they contribute to the overall corporate strategy. It includes technical knowledge for non-technical people and business knowledge to technical people. For this category of knowledge we provide pieces of trainings because this way we can ensure that everyone has the complete knowledge set to be a high-performer in our company.
Learning Day
The Learning Day is our knowledge-driving initiative and it occurs on the last Tuesday of each month. It is a whole day dedicated to Learning. We start with breakfast at 9h00 filled with brain booster food and after that, we start the training according to the following formats:
- Tech Challenges: consist of a presentation with an instructor that will act as a facilitator for the employee to assimilate the knowledge. After the training, employees receive a Tech Challenge to prove that they are capable of completing tasks relating to what they just learned.
- Tech Sessions: consist of a collaboration activity or open format seminar. It can be given by an external training and it also comes with a task to be completed that varies from topic to topic.
After the completion of a training, you will receive a challenge to prove you are capable of completing tasks related to what you just learned. They are usually short exercises to test you.
Subjects that we provide training
- Secure Group Knowledge – for this category of knowledge we provide pieces of training because this way we can ensure that everyone has the complete knowledge set to be a high-performer in our company.
Please note, if you attend training regarding some of these topics you need to score a grade 3 in the KAI related to the topic.
Subjects that we don't provide training
We don't provide training regarding topics that belong to Extensive Knowledge of any framework. We understand that this should be developed by our employees on a daily basis and it's a good practice that shows adherence to our value "Devotion to Learning" shown in the Culture Code (page 35 from Secure Group Management Model presentation on Secure Group Wiki's home page).
What's like to be a trainer/trainee in Secure Group?
Knowledge sharing is part of the Levels in our development path. In order to progress, employees must demonstrate the capability of sharing knowledge in a structured way and the capability of applying Tech Sessions.
Responsibilites
| Instructor's responsibilities | Manager's responsibilities | Management Model Expert's responsibilities |
|---|---|---|
|
|
|
Knowledge Accountability Index
We already established that we keep “good” processes that promote accountability. The same applies to knowledge. In order to measure, manage the existing knowledge in the company and to promote accountability we created a Knowledge Accountability Index a.k.a. KAI.
The KAI is an instrument used to view everyone’s ability and competency in a specific occupation. It also measures all the technical skills and knowledge sets a person needs to progress. The KAI is divided into two categories: Extensive Knowledge and Secure Group Knowledge.
The index captures a wide range of abilities and organizes them into five grades. These range from “Fundamental awareness” to “Expert”. The index can be used by an individual to compare their current level of proficiency to top performers in the same occupation and it enables us to:
- Centralize effort to understand technology trends from a holistic view
- Define knowledge as a key component in high performance
- Anticipate and adapt to changes in external/internal environments to obtain/retain a competitive advantage in a quantifiable structure
In Secure Group, the effective management of knowledge aids competitive advantage. When people are accountable for knowledge it can be shared more efficiently and productively. We have put in place systems and good processes to achieve this so armed with knowledge, our employees are better able to innovate in their work.
Company Knowledge Centricity Level
Our current situation is represented by Grade 1 and Grade 2 depending on of individual and department.
Goal
Our strategic goal is to achieve Grade 3 till spring and Grade 5 by next year
| Secure Group Centricity Grade | ||||
|---|---|---|---|---|
| Knowledge Centricity Grade | Grade Description | Capabilities | Value Delivered | Knowledge Footprint |
| Grade 1 | Inability to generate actionable knowledge |
|
Understanding on an ad hoc, post-mortem basis as to why it happened. | Little Knowledge infrastructure. |
| Grade 2 | Knowledge silos within the organization. |
|
Understanding of business and issues which must be addressed to improve individual business units/functions. | Analytical resources embedded in local functional teams. |
| Grade 3 | Aspire to leverage knowledge. |
|
Ability to capture current conditions, attempt to understand future trends model in place. | Local knowledge delivery Model in place. |
| Grade 4 | Knowledge-Driven Business |
|
Ability to anticipate I adapt to changes in external/internal environments to obtain/retain competitive advantage analytical structure. | Central enterprise-wide knowledge structure. |
| Grade 5 | Industry Knowledge Leader |
|
Generate consistent business value through insights to obtain competitive advantage established analytical processes embedded in over competition organization. | Well established knowledge process embedded in the organization. |
Why is it failing
1. Inefficient when it serves only individuals. When an employee or a prospect gains information from another person – say, via email or through a conversation, this knowledge has been transferred to a grand total of one person. It takes time and diligence to convey knowledge – and to go through that effort for one person alone is completely inefficient. There are likely dozens, if not hundreds or thousands of other stakeholders who might be in need of the exact same information. That’s a lot of emails or phone calls.
2. Reckless with employees’ time because it’s repetitious. In most cases, stakeholders will get answers and information in a one-on-one conversation. (For instance, an employee asks a colleague a question or a prospect visits the location to talk with a staff member.) This knowledge transfer process is hardly even a process; it’s disruptive and time-consuming. When a handful of Subject Matter Experts are heavily relied upon to provide information verbally, they’re interrupted frequently to answer the same questions over and over by different people – they spend their time repeating the same information when they could be doing more value-added work.
3. Ineffectual because it’s impermanent. According to the latest research, it’s extremely difficult for humans to remember information they learned even just a few days ago. This problem – illustrated in the Curve of Forgetting – is exacerbated if the person learned this information verbally. That’s just a reality of the human brain. So not only was the process to acquire the information time-consuming and wasteful, it wasn’t even effective. The person probably has forgotten some or most of the knowledge and will be forced to seek it out again.
4. Uncontrolled because no one is accountable. A non-existent or ill-thought-out knowledge transfer process means that no one can be held accountable to be sure the information they have is accurate and up-to-date. When managers and company leadership don’t know:
- What they need their team to know
- What their team already know and if it is correct
- What their team do not know
- If the accurate information is readily available to all relevant members of the team
No one can hold employees accountable to own the correct knowledge and to leverage it appropriately. This means staff can be wasting time looking for answers, providing incorrect, incomplete, or outdated information to prospects and customers, not following the wrong processes and guidelines – and there’s no proper way to assess their work, correct them, or monitor their improvement afterward.
5. A self-fulfilling prophecy that's bound to reoccur. Though stakeholders may be willing to go to some effort to find and learn the knowledge they need, when the process stops after they’ve got the information they want, the organization misses out on a key opportunity to streamline their process, reduce repetition, and better serve others. Aside from the knowledge giver and recipient, no one else is aware of the gap that existed in the first place – thus, no one can prevent this situation from reoccurring.
Where knowledge should not be
1. In previously published content: For example, Ivan might dust off his old training manual or search on the company intranet to look for the answer. The problem? This is time-consuming – especially since the information may not even be there, or could be outdated. Worse, the information might actually be present in other materials of which Ivan isn’t aware or to which he does not have access.
2. In somebody’s brain: Ivan fastest option is to ask one of his colleagues. He might email, call, or have a conversation with a co-worker. But if the particular expert he needs is out sick, too busy to talk, or simply makes a mistake, Ivan either has an incorrect answer or no answer at all. In addition, he has also disrupted that employee from his or her tasks.
3. In the cloud: Sometimes, the knowledge exists in a sub-space that isn’t formally published content, but has been recorded. For instance, Ivan might find the answer sifting through his archived emails, memos, company updates, or notes. Chances are its obscure, ill-explained, and hard to find.
Knowledge Grade Description
This scale serves as the guide to understanding the expected proficiency in each grade.
| Grade | Name | Description | Focus |
|---|---|---|---|
| 1 | Not Applicable. | You are not required to apply or demonstrate this competency. This competency is not applicable to your position. | |
| 2 | Fundamental awareness (Basic knowledge) | You have a common knowledge or an understanding of the basic techniques and concepts. | Focus on learning. |
| 3 | Limited experience (Novice) |
|
Focus on developing through on-the-job experience. |
| 4 | Practical application (Intermediate) |
|
Focus is on applying and enhancing knowledge or skill. |
| 5 | Applied theory (Advanced) |
|
Focus is on broad organizational/professional issues. |
| 6 | Recognized authority (Expert) |
|
Focus is strategic. |